System Architecture and Secure Data Processing
Client Library Integration
The system provides a dedicated Java library for client integration.
Integration Details
- Library Location: https://mvnrepository.com/artifact/io.bitdive
- Type: Java Library
- Purpose: Client-side integration for secure file processing
Maven Integration
<dependency>
<groupId>io.bitdive</groupId>
<artifactId>bitdive-producer-spring-3</artifactId>
<version>0.0.15</version>
</dependency>
Usage
- Add the dependency to your Java application
- Initialize the client with appropriate configuration
- Use the provided methods for secure file processing
System Architecture Overview
The system consists of multiple microservices designed to handle secure file processing, storage, and data management.
Architecture Diagram
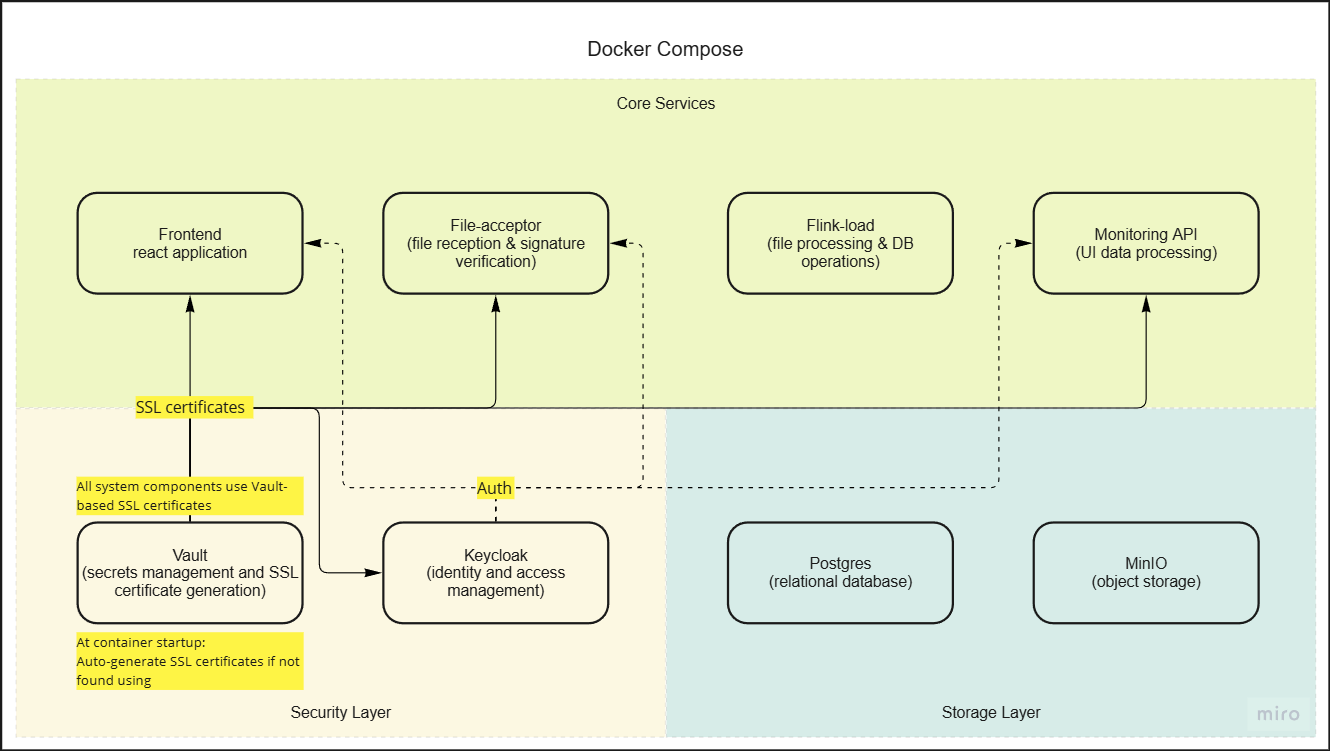
Key Components
Core Services
- Frontend: User interface service
- File Acceptor: Handles file reception and signature verification
- Flink Load: Processes files and manages database operations
- Monitoring API: Handles UI data processing and monitoring
Infrastructure Services
- Vault: Manages secrets and SSL certificates
- PostgreSQL: Primary database for structured data
- MinIO: Object storage for files
- Keycloak: Identity and access management
Security Features
- Automated SSL certificate generation on container startup
- Vault-based SSL certificate management
- Secure service-to-service communication
File Transfer Process
This section describes the secure process of transferring files from client to server.
Process Diagram
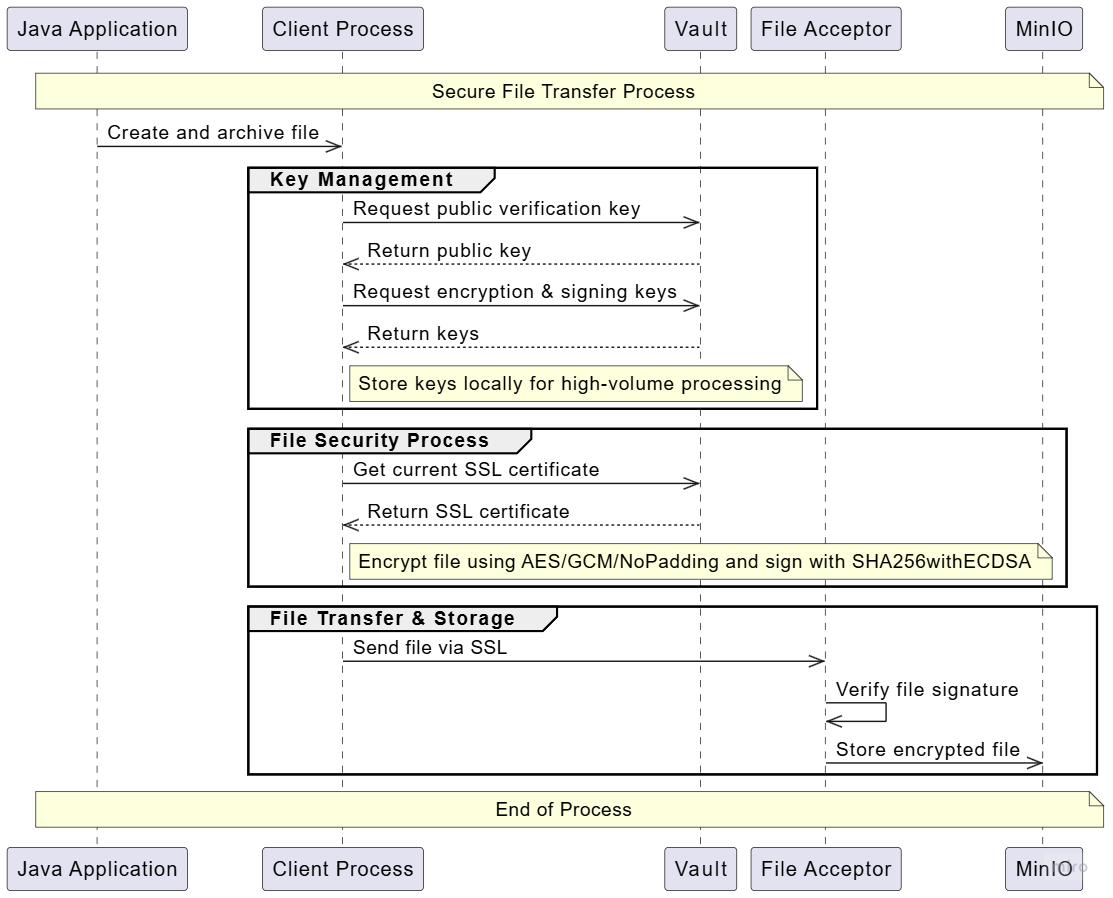
Process Steps
-
Initial File Preparation
- Java application prepares and archives files
- Files are prepared for secure transfer
-
Key Management
- Public key retrieval for signature verification (24-hour rotation)
- Encryption and signing key management
- Local key storage for high-volume processing
-
Security Measures
- AES/GCM/NoPadding encryption
- SHA256withECDSA file signatures
- SSL-secured transfer
-
File Storage
- Signature verification on receipt
- Encrypted storage in MinIO
File Processing and Database Integration
Details the process of processing files and integrating data into the database.
Process Diagram
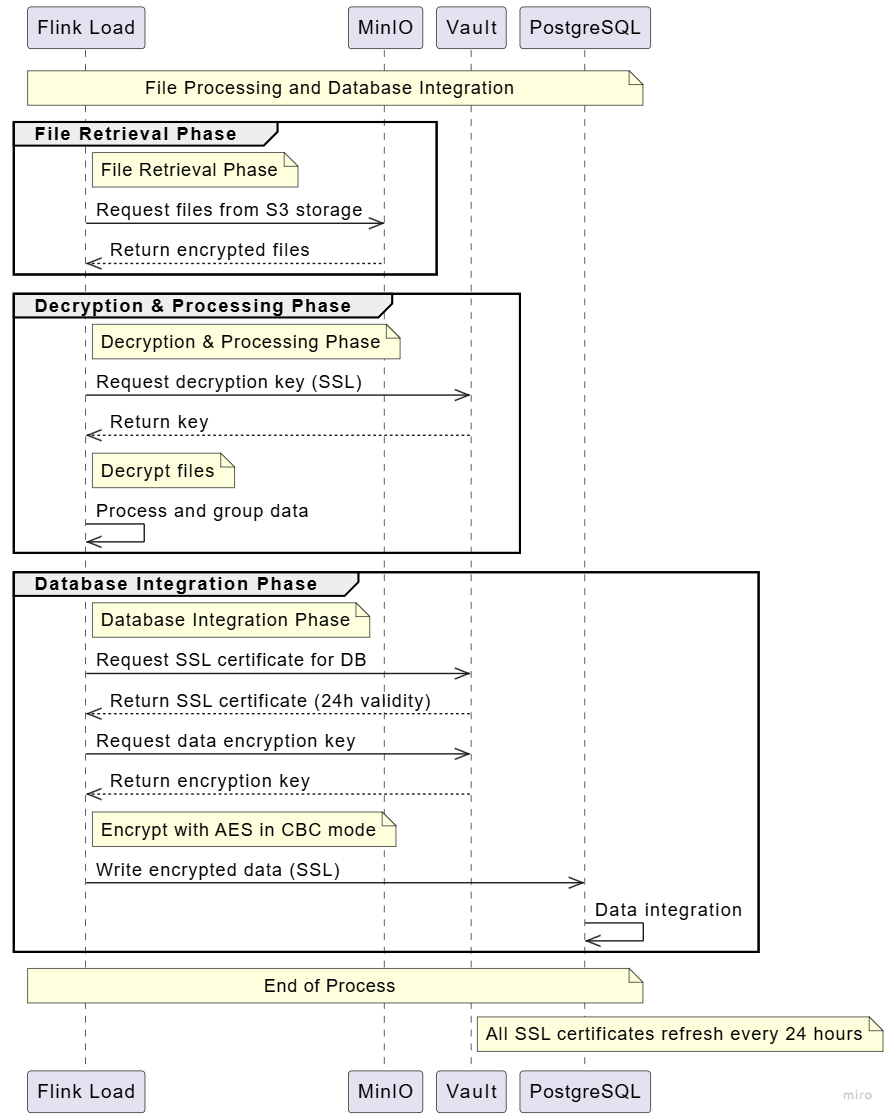
Process Flow
-
File Retrieval
- Secure retrieval from MinIO storage
- Encrypted file handling
-
Processing
- Secure key retrieval from Vault
- File decryption
- Data processing and grouping
-
Database Integration
- SSL certificate management (24-hour rotation)
- AES CBC mode encryption
- Secure PostgreSQL integration
Frontend Operations
Describes the frontend interaction with backend services.
Process Diagram
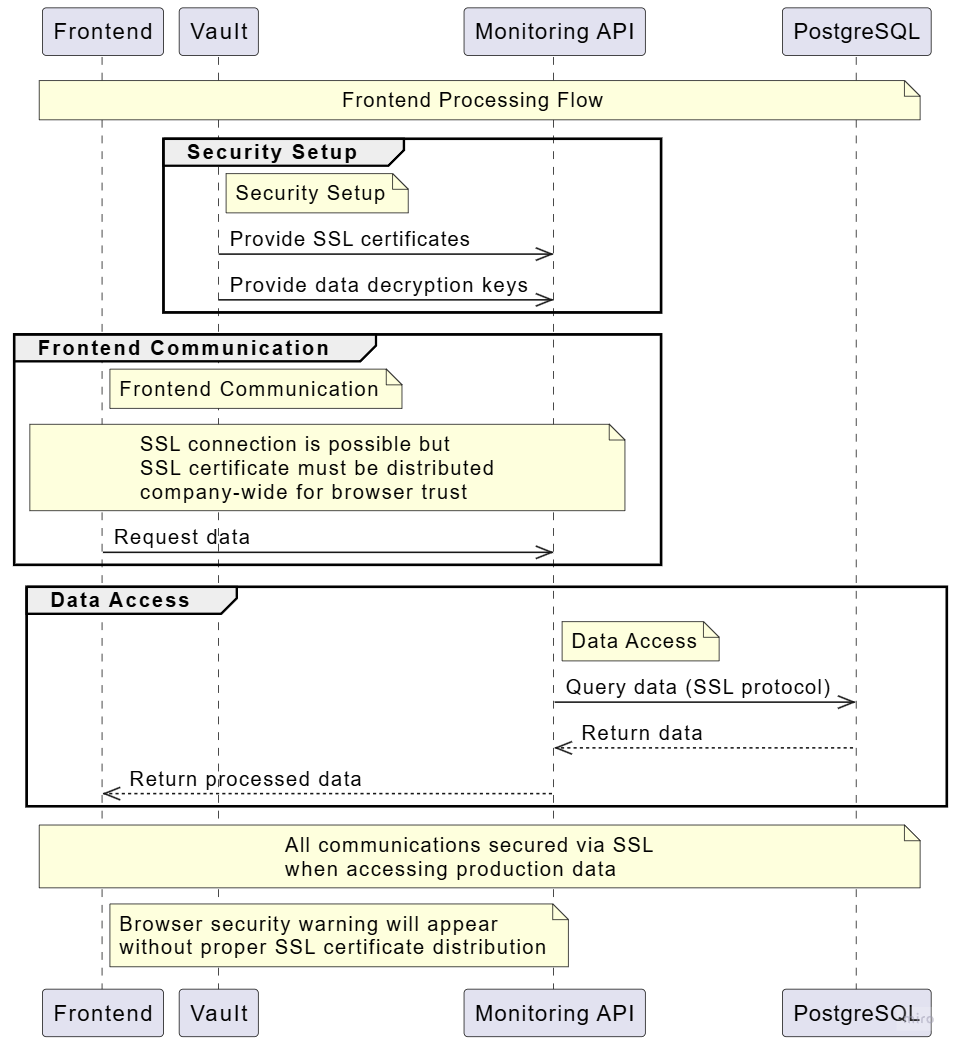
Security Considerations
-
SSL Implementation
- SSL connection support
- Company-wide certificate distribution required
- Browser trust management
-
Data Flow
- Secure communication with Monitoring API
- SSL-protected database queries
- Encrypted data handling
Important Notes
- SSL certificates must be properly distributed to prevent browser trust issues
- All production data access requires SSL encryption
- Regular certificate rotation ensures security
- Browser security warnings will appear without proper certificate setup
Security Best Practices
- Regular certificate rotation (24-hour cycle)
- Encrypted data storage
- Secure key management
- SSL implementation throughout
- Regular security audits
- Proper certificate distribution
System Requirements
- Docker and Docker Compose
- Java Runtime Environment
- SSL Certificate Infrastructure
- Adequate Storage for MinIO
- PostgreSQL Database System
- Network Security Infrastructure
Troubleshooting
-
Browser Trust Issues
- Verify SSL certificate distribution
- Check certificate validity
- Ensure proper certificate installation
-
File Transfer Issues
- Verify key availability
- Check SSL certificate status
- Confirm proper encryption
-
Database Connection Issues
- Verify SSL configuration
- Check certificate rotation
- Confirm security protocol compliance